We talked a lot about FSMO roles and their purpose on previous articles in my blog. The FSMO roles, I used to ask this question all the times
Which FSMO role is the most important considering one single domain / Forest. Or the opposite one, which FSMO role is the less important one considering one domain.
Answer of course will vary from person to another. The reality is that PDC emulator is the mostly, heavy used FSMO roles among others.
Another FSMO question is how to see FSMO roles? Those of you who have hands on experience will know ADUC is the first place to go and look for Domain wide FSMO roles
When a right clicks on ADUC and select Operations masters
- RID
- PDC
- Infrastructure
Seizing is kid stuff, fist connect to DC you wish to transfer these roles too, by opening ADUC and choosing connect to domain controller. Once you connect to the domain controller now open up the operation masters and start seizing them one by one
The forest ones requires same type of afford, only schema master needs a DLL file to be registered
Register Schmmgmt.dll
Go to command line or run menu copy or paste below and hit enter
regsvr32 schmmgmt.dll
Now we will seize the domain wide FSMO roles
Click start, run, and mmc, add snap in and select Active directory Schema snap in and select Active directory domains and trust snap in, click ok.
Same technique will apply here, first make a right click all the way top and select connect to domain controller ( this is the DC you are trying to transfer the FSMO role too) , once you connect to selected DC all you need to do is , another right click and "Operations Masters) and click change
Same applies for the Domain Naming Master Role.
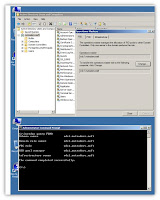
Now, how to see all the FSMO roles one at the time is the question. Several different ways, including GUI and third party tools available to achieve this mission.
The easiest one I can think of would be Download support tools, and install it. Go to CMD and type following command
Netdom query fsmo
C:\>netdom query fsmo Schema owner vdc1.nwtraders.msft Domain role owner vdc1.nwtraders.msft PDC role vdc1.nwtraders.msft RID pool manager vdc1.nwtraders.msft Infrastructure owner vdc1.nwtraders.msft The command completed successfully. |
Seize FSMO roles from command line
Schema master Domain naming master RID master PDC Infrastructure master | Forest wide and one per forest. Forest wide and one per forest. Domain specific and one for each domain. PDC Emulator is domain specific and one for each domain. Domain specific and one for each domain. |
- Log on the DC open CMD
- Type following
- Ntdsutil, hit enter
- Roles ( you can use ? to see the available commands)
- Fsmo maintenance
- Connections
- Connect to server <Server name goes here>
- q
- Seize domain naming master
A windows will open up and will ask you sure you want to do this , click yes
All roles can be seized as below table
Seize domain naming master Seize infrastructure master Seize PDC Seize RID master Seize schema master |
Each time you will get the same warning
Best,
Oz ozugurlu
MCITP (EMA) ,MCITP(SA),
MCSE (M+,S+) MCDST
Security+, Server +,Project+

No comments:
Post a Comment