Exchange Server system mailbox is also called "Arbitration" mailbox. Exchange Server uses these mailboxes for various tasks. These mailboxes are being created when you setup first exchange server preparing Active Directory /PrepareAD in the root domain of the AD Forest.
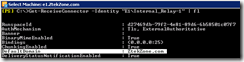
if you would like to locate these mailboxes you would use get-mailbox –Arbitration cmdlet and if you are in the root and child domain environment, you have to adjust the PS search to look at the root of the forest to locate these accounts.
| Set-ADServerSettings -ViewEntireForest $true Get-mailbox -Arbitration | fl name,Database,DisplayName,ServerName |
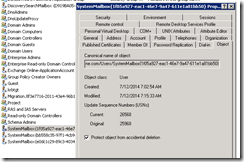
- Name : SystemMailbox{1f05a927-eac1-46e7-9a47-611e1a81bb50}
- Name : SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}
- Name : SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}
- Name : Migration.8f3e7716-2011-43e4-96b1-aba62d229136
If you go to root of your active directory forest you will be able to locate the user accounts associating with these system mailboxes.
By default they are located at the users container in the root of the AD Forest.
Arbitration system mailboxes keeps & stores organization wide data in them such as
- eDiscovery Searches Metadata ( if you are using search-mailbox cmdlet with –targetmailbox switch and offloading searched enterprise data, before deleting the Arbitration system mailboxes could get potential big with the metadata collection as repository)
- Administrator audit logs ( Ability to run Search-AdminAuditLog cmdlet )
- Unified Messaging data, such as menus, dial plans, and custom greetings
In most of the cases these account you wont pay huge attention , as they are not exposed to EMC and there is less chance them getting deleted. To be better prepared you can turn on “Protect object from accidental deletion” on these accounts.
You can do same work from PS , the most common way is to ask for help if you do not remember the cmdlet
import-module ActiveDirectory
Get the help you need
| Get-Help Get-ADUser -examples |
Look for System Mailboxes
| Get-ADUser -Filter 'Name -like "SystemMailbox*"' | FT Name |
Enable all at once.
| Get-ADUser -Filter 'Name -like "SystemMailbox*"' | Set-ADObject -ProtectedFromAccidentalDeletion:$true |
Scenario –1
You have decided to move these mailboxes onto another database
Specify the target database with new-move Request
| Get-Mailbox -Arbitration -Identity "SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}" | New-MoveRequest -TargetDatabase DB200 |
Scenario – 2
You decided to delete the System mailbox while preserving AD Account so you can create new Arbitration System mailbox
List the Arbitration mailboxes
Get-mailbox -Arbitration | fl name
- Name : SystemMailbox{1f05a927-eac1-46e7-9a47-611e1a81bb50}
- Name : SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}
- Name : SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}
- Name : Migration.8f3e7716-2011-43e4-96b1-aba62d229136
| Get-mailbox -Arbitration -Identity "SystemMailbox{1f05a927*" | Disable-Mailbox –Arbitration –Confirm:$False |
AD account is still exist, we will create brand new arbitration mailbox for the same account.
| Enable-mailbox -Arbitration -Identity "SystemMailbox{1f05a927*" |
Scenario – 3
Arbitration mailboxes AD account has been deleted , simply re-run setup
If you have Exchange 2013 in the environment you need to run the setup from E2013 media.
| Setup.EXE /IAcceptExchangeServerLicenseTerms /PrepareAD |
Simple enough after setup is complete, they are back.
Respectfully,
Oz Casey, Dedeal ( MVP north America)
MCITP (EMA), MCITP (SA)
MCSE 2003, M+, S+, MCDST
Security+, Project +, Server +
http://smtp25.blogspot.com/ (Blog)
http://telnet25.wordpress.com/ (Blog)