We would like to utilize RBAC Role model and create custom RBAC Role for specific needs for a business. These needs could be different from one environment to another. This article will be good reference for you to get your customization. Having said that, first thing to understand is the RBAC Layers.
There are 6 Layers which make up the Role Group Model
- Role group member
- Management role group
- Management role assignment
- Management role scope
- Management role
- Management role entries
Goal:
- Create Custom Role Group
- Create Custom RBAC Role Entry with desired cmdlet's
- Add Custom Role entry to Role
- Add role to Custom Role Group
- Add Members to Custom Role Group
In this example we will use following template
Note: You can build your own management Role , and modify management role entries same way in this article. The process is pretty straight forward.
Task#1
Figure out all role entry contains set-mailbox (set-mailbox is one of the cmdlet we have as our requirement)
| Get-ManagementRoleEntry *\Set-Mailbox |
Task#2
Create the management role with related parent Role
| New-ManagementRole -Name “Assign Mailbox Access” -Parent “Mail Recipients” |
Task#3
| Get-ManagementRoleEntry "Assign Mailbox Access\*" |
Verify all cmdlet assign to newly created management role, as you can see we have many cmdlet we don’t want, therefore we will need to remove most of them and only keep what we need.
Task#4
Remove what you don’t need
| Get-ManagementRoleEntry “Assign Mailbox Access\*” | Where {$_.name -ne “Add-MailboxPermission”} | Remove-ManagementRoleEntry -Confirm:$False |
Task#5
Verify the Role entry , minimum cmdlet is assigned.
Task#6
Add additional cmdlet
- Add-ManagementRoleEntry "Assign Mailbox Access\get-mailbox"
- Add-ManagementRoleEntry "Assign Mailbox Access\get-mailboxPermission"
- Add-ManagementRoleEntry "Assign Mailbox Access\remove-mailboxPermission"
- Add-ManagementRoleEntry "Assign Mailbox Access\set-mailbox"
Task#7
Add remove any role entries if desired
Verify one more time to make sure we have all we wanted. If required continue to add by using same one liner cmdlet
Add-ManagementRoleEntry "Assign Mailbox Access\set-mailbox" ---------------> you can replace set-mailbox
If you need to remove use
Remove-ManagementRoleEntry "Assign Mailbox Access\set-mailbox"
Task#8
Create new Role Group
| New-RoleGroup “Audit Team” |
Task#9
Let's put them together
| New-ManagementRoleAssignment -SecurityGroup "Audit Team" -Role "Assign Mailbox Access" |
Task#10
| Add-RoleGroupMember “Audit Team” –Member C-Ron.Buzon |
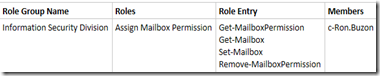
We are done lets look at this from ECP
Now if c-ron.Buzon logs in, he will only get the cmdlets assigned to him via RBAC Role. As you can see RBAC permissions model is very efficient and effective. When creating Roles, group and Role entries, you may want to think about unifying name convention and plan this out before start implementing it into production environment.
Respectfully,
Oz Casey, Dedeal ( MVP north America)
MCITP (EMA), MCITP (SA)
MCSE 2003, M+, S+, MCDST
Security+, Project +, Server +
http://smtp25.blogspot.com/ (Blog)
http://telnet25.wordpress.com/ (Blog)

![clip_image001[4] clip_image001[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg1IcWCjb8U5qnIQzDZh7G5PpVXyJoTEAxhzRSCiYfvXNLEp5w3p9iMMZSdG2zDwpuqlorB7LtC6Dg7KxxWkS_Y0y2SfpGKWdvkg6W2qkNPbQsjsrRsnenC97wiflZ7tdiaQ8vlt0jWPZI/?imgmax=800)
![clip_image002[4] clip_image002[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi2u3Cfql70AwzMHSoCz6wmCo2olQe0xK9vXxYyNMYKYMjrjAO2iBI0Qp38_q7Fc3EUUKiW1U0-FjtUbi_4vPHM-BssUXM1DlA1DotzGa_bio9atysdBrOkW-gQ84pngobyzYyKAy_ccf0/?imgmax=800)
![clip_image004[4] clip_image004[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgkNjMkZaT9URYnNsUHsK3XaW9j1r2C3Xkya4iOajnZqO2_1OV4NxcJmGDfq90PLyEw9RGDVIiKOuA1FN2c2dntZphoOmo5ghw8um-0plcUjmdUl_N4qQEo0EubkwTSFSHYR0ww1POQkg8/?imgmax=800)
![clip_image008[4] clip_image008[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgBwBzX4PJlT3XW9jVosZyU62RxDDu_LNY6avU7t4VWeL-Z2oAo31EdkrzoTkdgXjrtWaI_9QOd_O4C5FzTlaxEWZ9Jv8Dw6hRftPoQnZD5I6smQhFb-USmEwx1KcAIFrGns9QZNxoOi-I/?imgmax=800)
![clip_image009[4] clip_image009[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi1XOjDvjiq7grNnkO3Ir5D6RkRA7tvJlpW5J91NSGNrawCNUIIQAQM0sBWXQcoCHQB1vTu2II9NJiivEA5yvUHkbHYDa2vDwFSn0N7WTrS2JW-a3o86YJAVxdcq3pnpHOhpnJBj1tJwbU/?imgmax=800)
![clip_image012[4] clip_image012[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhyEgsLDSzcDSABWW7KNPLszRX1jPWoMNZf5VVV8POrHHHLYtc6nwMYSUtbE2gkax2Nyam6BcGnIBzHy45KBiuXbLn4-gtqX1CLLFHf29DXP8W9Fbn3MozAZ7NTe4X-sJ7i9rWEmcO8lBs/?imgmax=800)
![clip_image013[4] clip_image013[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjTJ086NFOkQPd-_DKeYQPdHrXqJu9Qe-rk5YX8gR_f0-4wv9r9kp9l-4a1eoSs0TZw85a30oE1Fzs6FqgwFR8PICqMJtmbA2YsloRcdLPiVVuURb3ttaOhOffhwcX01ZXhYJEW1zW_Ubk/?imgmax=800)
1 comment:
Images are too small....
Post a Comment